Ubiquiti has been in the tech news recently, and not for good reasons. That, however, is not what this post is about.
I occasionally deign to log in to my local UniFi controller that’s running on the same Pi that runs my Pi-Hole installation. Did so two days ago, and there was a firmware update available for the two in-wall UAPs and the 8 port PoE switch that I have. Fine, I’ll upgrade. Should be fine, right?
Wrong.
Firmware 4.3.28.11361 for the UAP appears to completely hork the ability to pass DHCP OFFER packets back to the iPhone. Downgrade to 4.3.20.11298 and the phone instantly gets an IP from the DHCP service running on the OpenWRT install.
Ubiquiti do not make it easy to do a downgrade either – it’s accessed from the controller view of the device, via the config option, then manage device, and selecting custom upgrade, specifying a URL that points to the .bin file. The controller also has the ability to cache firmware, so you can update your fleet from the controller’s cache. Is that cache URL easily visible anywhere? No. Does the custom upgrade field perchance offer a dropdown of local versions? No.
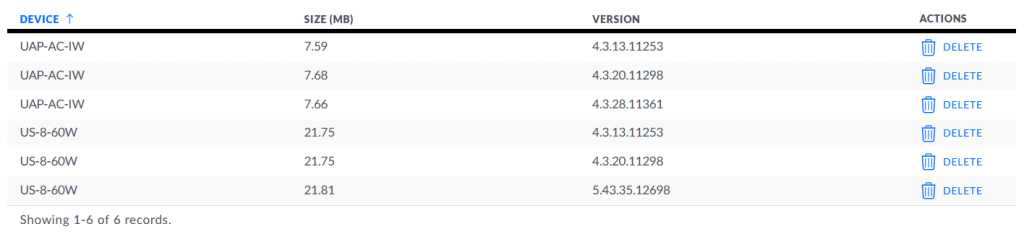
I eventually found a post that talks about “http://ip.of.the.controller:8080/dl/firmware-cached/<the model>/<version>/<firmware-checksum>.bin”, and after logging in to the Pi and looking around, I found /var/lib/unifi/firmware with a nice tree underneath it of models (which are not the model names you see in the UI.. good going Ubiquiti), and was able to work out that /dl/firmware-cached/ maps to /var/lib/unifi/firmware. From that, I can construct the relevant URL to custom upgrade the UAP with an older firmware.
Eesh.
I suppose I should file a bug report with Ubiquiti about the firmware.
Have to say though, other than breakages like this, I don’t actually notice my AP infrastructure. It just works, and the wall-based UAPs are pretty discreet (once you turn off the blinding blue LED). The oddity is that they take a 8P8C (RJ45) connector on the back, not a standard punch terminal like any other jack. Makes things a little more annoying when the backbox is a bit too shallow for a good curve radius.